The Conflux Network is a high-throughput public blockchain designed to support decentralized applications (DApps), e-commerce, and Web 3.0 infrastructure. As the only regulatory-compliant blockchain in China, it employs a variety of advanced security measures to ensure the integrity and safety of its ecosystem. This article delves into the security protocols and strategies employed by Conflux to protect its network, highlighting market trends, implementation strategies, risk considerations, regulatory aspects, and future outlook.
| Key Concept | Description/Impact |
|---|---|
| Tree-Graph Consensus Mechanism | A layered consensus protocol that enhances throughput and security by allowing parallel processing of transactions across multiple sub-chains. |
| Interference-Free Protocol | Ensures nodes can independently select parent blocks without being influenced by others, enhancing decentralization and security. |
| Random Function Utilization | Generates random numbers to ensure fairness in the consensus process, reducing the risk of manipulation by malicious nodes. |
| Bug Bounty Program | A proactive approach to security that invites researchers to identify and report vulnerabilities, incentivizing community involvement in maintaining system integrity. |
| Smart Contract Security Protocols | Includes comprehensive testing, auditing practices, and adherence to best practices to mitigate vulnerabilities in deployed contracts. |
| Adaptive Difficulty Adjustment | Dynamically adjusts mining difficulty and rewards to maintain network stability and miner profitability while ensuring security. |
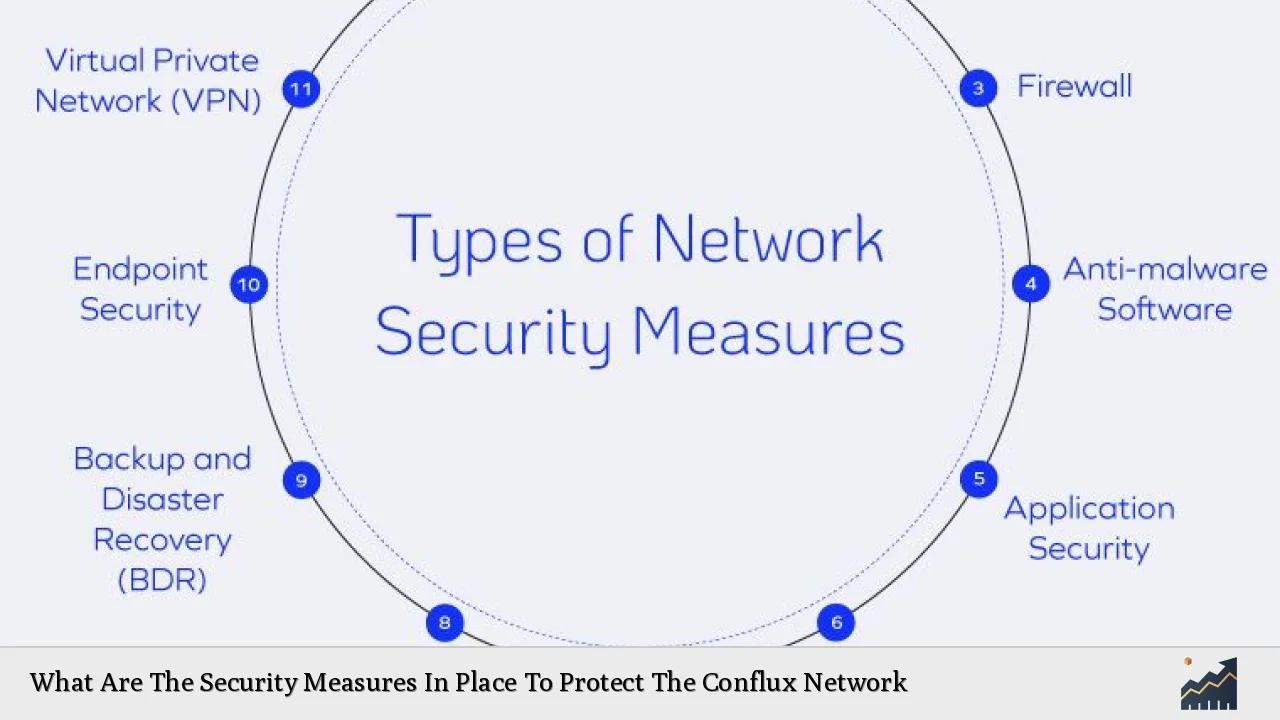
| Wallet Security Measures | Guidelines for secure wallet creation and management, including the use of secure devices and environments to prevent unauthorized access. |
Market Analysis and Trends
The Conflux Network operates within a rapidly evolving blockchain landscape characterized by increasing demand for secure and scalable solutions. As of December 2024, Conflux’s market capitalization stands at approximately $1 billion, with a circulating supply of about 4.72 billion CFX tokens. Recent trading volumes have shown significant fluctuations, with a notable increase in interest following broader market trends favoring blockchain technologies.
The integration of regulatory compliance has positioned Conflux uniquely in the Chinese market, where governmental scrutiny is prevalent. This compliance not only enhances trust among users but also attracts institutional investors looking for reliable blockchain solutions.
Implementation Strategies
Conflux employs several key strategies to bolster its security framework:
- Layered Consensus Mechanism: The Tree-Graph structure allows for high transaction throughput while maintaining security through independent block validation.
- Interference-Free Consensus: This feature prevents nodes from being influenced by others during block selection, promoting a more decentralized network that is less susceptible to coordinated attacks.
- Randomized Block Generation: By utilizing random functions in block creation, Conflux minimizes the risks associated with predictable patterns that could be exploited by attackers.
- Robust Smart Contract Practices: Comprehensive testing methodologies—including unit testing, integration testing, and fuzz testing—are employed to ensure that smart contracts are secure before deployment. Regular audits by third-party firms further enhance this aspect.
Risk Considerations
Despite its robust security measures, the Conflux Network faces several potential risks:
- Smart Contract Vulnerabilities: Even with rigorous testing and auditing processes, vulnerabilities can still exist in smart contracts post-deployment.
- Market Volatility: The cryptocurrency market is inherently volatile; significant price fluctuations can impact user confidence and network participation.
- Regulatory Changes: As a blockchain operating under Chinese regulations, any shifts in policy could affect operational capabilities or user engagement.
- Phishing Attacks: Users remain vulnerable to phishing attacks aimed at compromising wallet security. Continuous education on recognizing such threats is essential.
Regulatory Aspects
Conflux’s commitment to regulatory compliance is a cornerstone of its operational strategy. By aligning with local regulations:
- It ensures that its platform is accessible to a broader audience while minimizing legal risks associated with operating in a heavily regulated environment.
- The Bug Bounty Program serves as an additional layer of compliance by actively engaging the community in identifying potential vulnerabilities before they can be exploited.
Future Outlook
The future for the Conflux Network appears promising as it continues to innovate within the blockchain space. Key trends that may influence its trajectory include:
- Expansion into Global Markets: As Conflux seeks to establish a presence outside China—such as in Dubai and Europe—it may attract new users and investors looking for compliant blockchain solutions.
- Increased Adoption of DApps: With growing interest in decentralized applications, Conflux’s ability to support high throughput will be crucial for attracting developers.
- Continued Investment in Security: Ongoing enhancements to security protocols will be vital as threats evolve. The community-driven approach through initiatives like the Bug Bounty Program will remain essential for maintaining trust.
Frequently Asked Questions About Security Measures in Conflux Network
- What is the Tree-Graph consensus mechanism?
The Tree-Graph consensus mechanism allows parallel processing of transactions across multiple sub-chains, enhancing both throughput and security. - How does Conflux ensure smart contract security?
Conflux employs comprehensive testing methodologies including unit tests, integration tests, fuzz tests, and third-party audits to secure smart contracts. - What role does the Bug Bounty Program play?
The Bug Bounty Program incentivizes community members to identify vulnerabilities within the network, enhancing overall system integrity. - Are there risks associated with using Conflux?
Yes, risks include smart contract vulnerabilities, market volatility, regulatory changes, and phishing attacks targeting users. - How does Conflux handle wallet security?
Conflux provides guidelines for securely creating wallets which include using secure devices and environments to prevent unauthorized access. - What measures are taken against malicious attacks?
The interference-free protocol ensures nodes make independent decisions during consensus processes, reducing susceptibility to coordinated attacks. - How does adaptive difficulty adjustment work?
This mechanism dynamically adjusts mining difficulty based on recent block generation speeds to maintain network stability while ensuring miner profitability. - What is the importance of regulatory compliance for Conflux?
Regulatory compliance enhances trust among users and attracts institutional investors looking for reliable blockchain solutions.
In conclusion, the Conflux Network employs a multifaceted approach to security that combines advanced technological measures with community engagement strategies. By continuously evolving its protocols and remaining vigilant against emerging threats, Conflux aims to establish itself as a leader in the blockchain space while ensuring user safety and confidence.