Orca Security, a prominent player in the cloud security market, has gained significant attention for its innovative approach to protecting cloud environments. As organizations increasingly rely on cloud infrastructure, the security of platforms like Orca becomes paramount. This comprehensive analysis delves into Orca Security’s track record, examining whether the company has ever experienced a hack or compromise, and exploring the broader implications for cloud security.
| Key Concept | Description/Impact |
|---|---|
| Orca Security’s Market Position | Leading provider of agentless cloud security solutions, gaining momentum in the market |
| Cloud Security Importance | Critical for protecting sensitive data and maintaining operational integrity in cloud environments |
| Vulnerability Disclosure | Orca Security has identified and responsibly disclosed vulnerabilities in major cloud platforms |
| Cybersecurity Landscape | Rapidly evolving with increasing sophistication of threats targeting financial and cloud services |
Market Analysis and Trends
The cloud security market has experienced significant growth, with Orca Security emerging as a key player. According to 451 Research, Orca’s agentless approach to cloud security is gaining traction due to its alignment with common customer pain points, particularly challenges related to agent deployment and alert overload. This market positioning has placed Orca at the forefront of cloud security innovation.
In the broader cybersecurity landscape, financial services have become prime targets for cyberattacks. The International Monetary Fund (IMF) reports that in the past two decades, nearly one-fifth of reported cyber incidents have affected the global financial sector, resulting in $12 billion in direct losses. This trend underscores the critical need for robust security solutions across industries, including those provided by companies like Orca Security.
Implementation Strategies
Orca Security’s implementation strategy focuses on providing comprehensive visibility and security across cloud environments without the need for agents. This approach addresses several key challenges:
- Eliminating the operational overhead of agent deployment and management
- Providing instant visibility into cloud assets and configurations
- Identifying vulnerabilities, misconfigurations, and compliance issues
- Offering context-aware prioritization of security risks
The company’s strategy aligns with the growing demand for efficient and effective cloud security solutions, particularly as organizations accelerate their digital transformation initiatives.
Risk Considerations
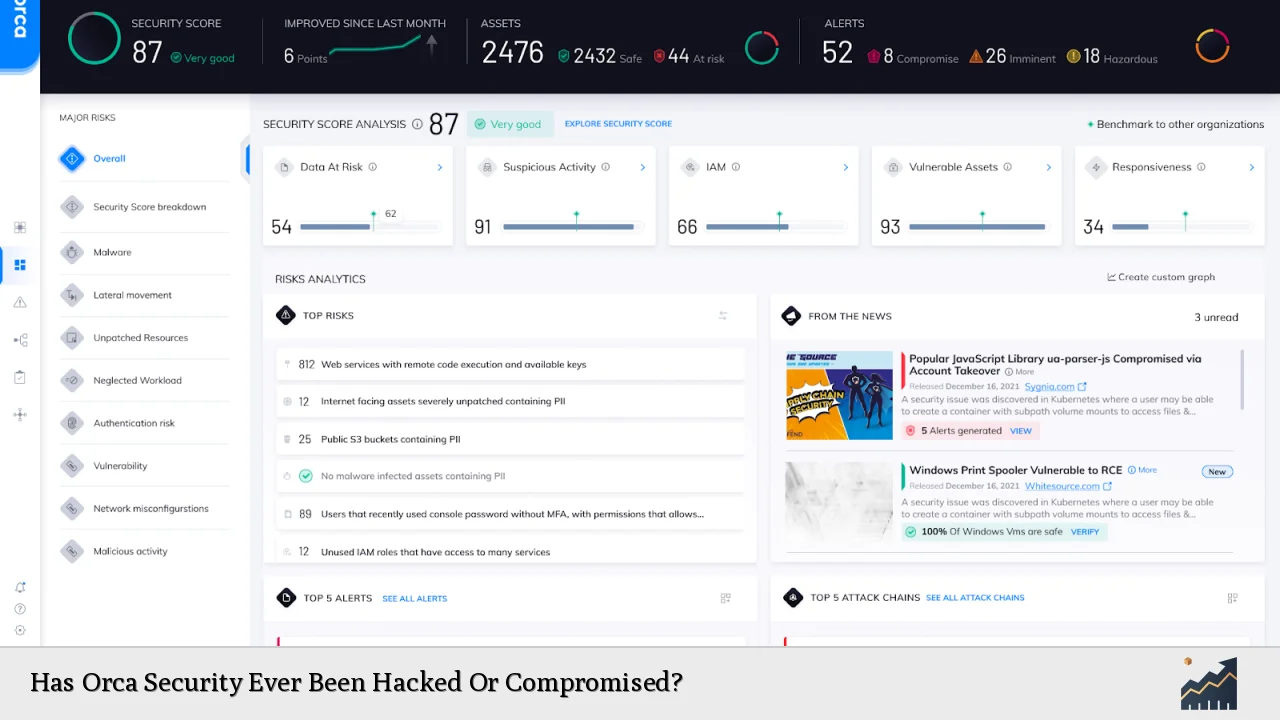
While Orca Security has not been publicly reported as being hacked or compromised, the company operates in a high-risk environment where the potential for cyber threats is ever-present. Several factors contribute to the risk profile:
Increased Targeting of Security Providers: Cybercriminals often view security companies as high-value targets, seeking to exploit their access to client data or undermine their credibility.
Evolving Threat Landscape: The cybersecurity field faces constant challenges from new and sophisticated attack vectors, requiring continuous adaptation and vigilance.
Cloud Infrastructure Vulnerabilities: As a cloud-native security solution, Orca Security’s effectiveness is partly dependent on the security of the underlying cloud platforms it monitors and protects.
Regulatory Aspects
The regulatory landscape surrounding cloud security and data protection has become increasingly complex. Orca Security must navigate a myriad of regulations, including:
- General Data Protection Regulation (GDPR) in the European Union
- California Consumer Privacy Act (CCPA) in the United States
- Industry-specific regulations such as HIPAA for healthcare and PCI DSS for payment card data
Compliance with these regulations is crucial not only for Orca Security’s operations but also for its ability to serve clients across various industries and geographies.
Future Outlook
The future of cloud security, and by extension Orca Security’s role in it, is shaped by several emerging trends:
AI and Machine Learning Integration: Advanced analytics and automated threat detection will become increasingly important in identifying and mitigating complex cyber threats.
Zero Trust Architecture: The adoption of zero trust principles is likely to accelerate, aligning with Orca’s approach to continuous monitoring and least-privilege access.
Multi-Cloud and Hybrid Environments: As organizations continue to diversify their cloud infrastructure, security solutions that can provide unified visibility and protection across multiple platforms will be in high demand.
Regulatory Evolution: Ongoing development of data protection and privacy regulations will require cloud security providers to maintain agility in their compliance capabilities.
In conclusion, while there is no public evidence of Orca Security being hacked or compromised, the company operates in a high-stakes environment where security is paramount. Its innovative approach to cloud security has positioned it well in the market, but ongoing vigilance and adaptation will be crucial to maintaining its security posture and market leadership.
Frequently Asked Questions About Has Orca Security Ever Been Hacked Or Compromised?
- What makes Orca Security different from traditional cloud security solutions?
Orca Security offers an agentless approach to cloud security, providing comprehensive visibility and protection without the need to install agents on every asset. This reduces operational overhead and allows for instant deployment across cloud environments. - How does Orca Security ensure the security of its own platform?
While specific details of Orca’s internal security measures are not publicly disclosed, the company likely employs industry best practices including encryption, access controls, regular security audits, and continuous monitoring of its infrastructure. - What would be the potential impact if Orca Security were to be compromised?
A compromise of Orca Security could potentially expose sensitive information about its clients’ cloud environments. However, the actual impact would depend on the nature and extent of the breach, as well as the specific data accessed. - How does Orca Security handle vulnerability disclosures?
Orca Security has demonstrated responsible disclosure practices by reporting vulnerabilities found in major cloud platforms to the affected providers before public disclosure, allowing time for remediation. - Can Orca Security protect against all types of cloud-based cyber threats?
While Orca Security provides comprehensive protection, no security solution can guarantee 100% protection against all threats. Its effectiveness lies in its ability to rapidly identify and prioritize risks, enabling organizations to address the most critical vulnerabilities first. - How does Orca Security’s approach compare to traditional antivirus or firewall solutions?
Unlike traditional security tools that focus on perimeter defense or endpoint protection, Orca Security provides a holistic view of the entire cloud environment, identifying misconfigurations, vulnerabilities, and compliance issues across all cloud assets.